Outstanding Info About How To Detect Ddos Attack

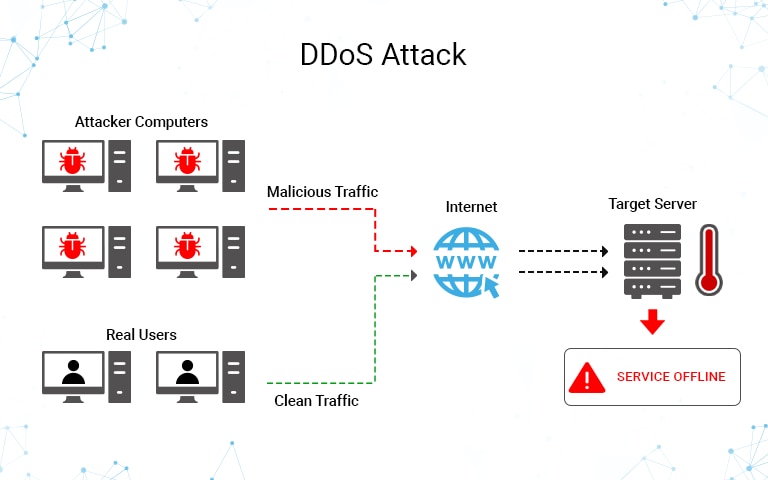
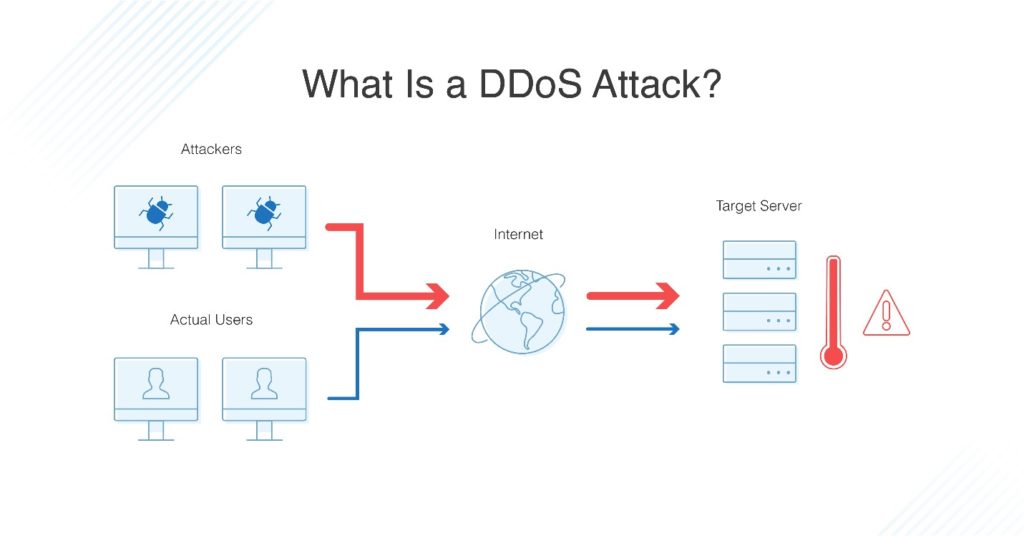
There are several clues that indicate an ongoing ddos attack is happening:an ip address makes x requests over y secondsyour server responds with.
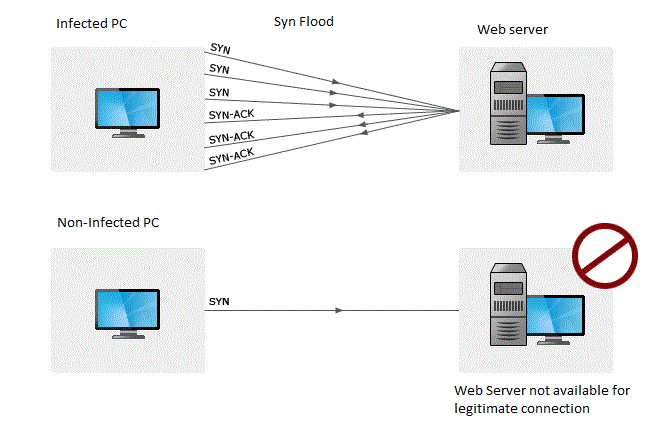
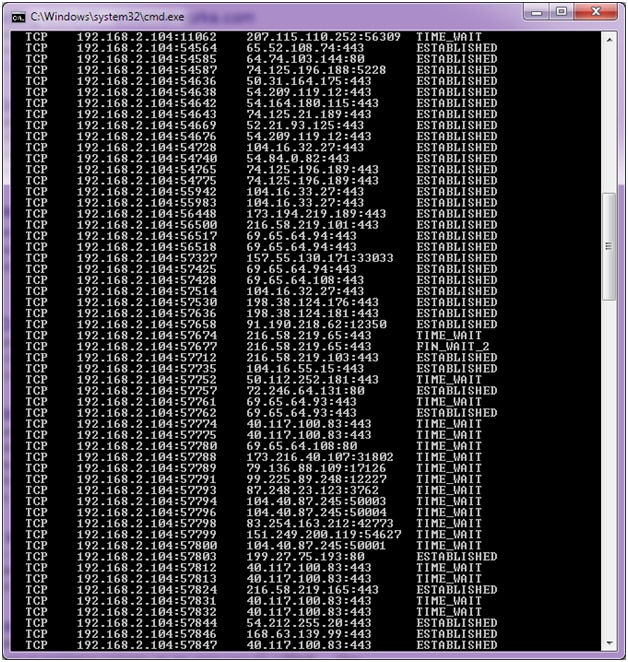
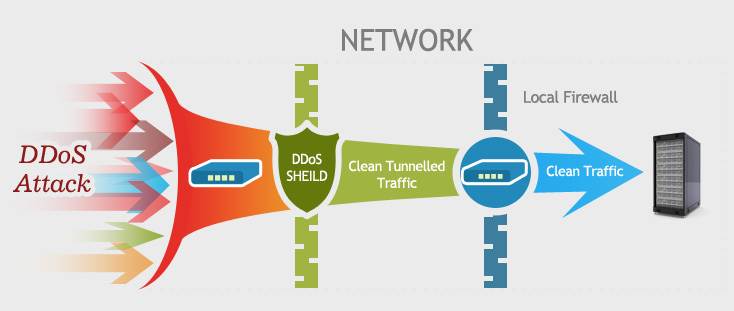
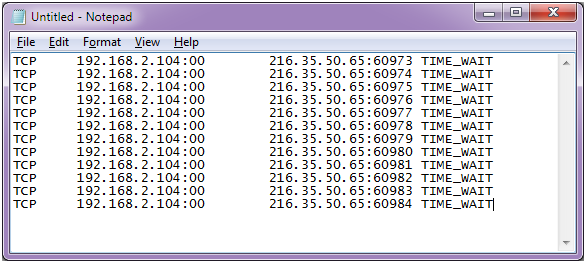
How to detect ddos attack. In the case of a ddos attack, the. Typically, these connections don’t get completed since. The /l switch indicates a “logoff” while the /f switch forces running applications to close.
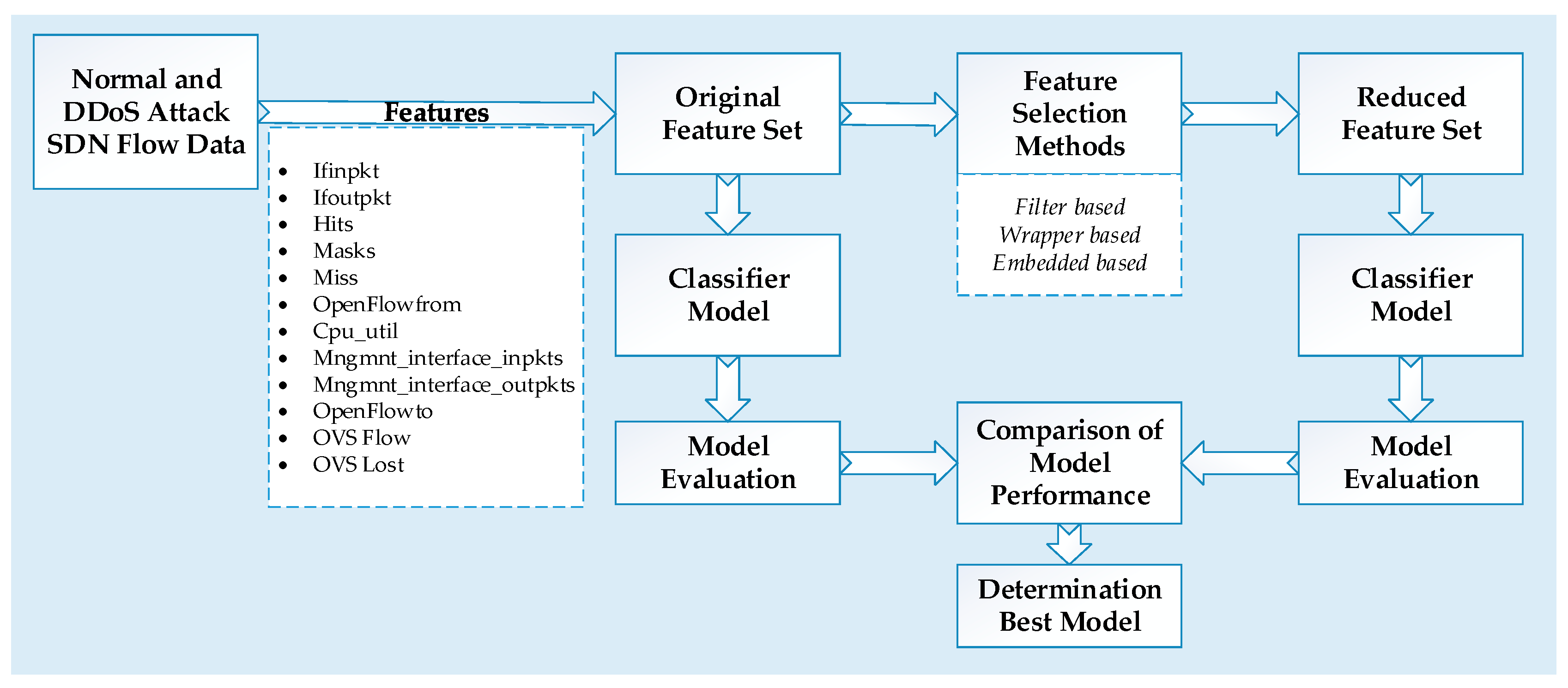
5 red flags when detecting ddos attacks. A graphical representation of the same is an easier way to understand abnormalities and guess a potential ddos attack. Ddos attacks are often used as a distraction while hackers execute their primary intention.
Open event viewer and right click on the event. Dns uses two types of packets: How to detect a ddos attack.
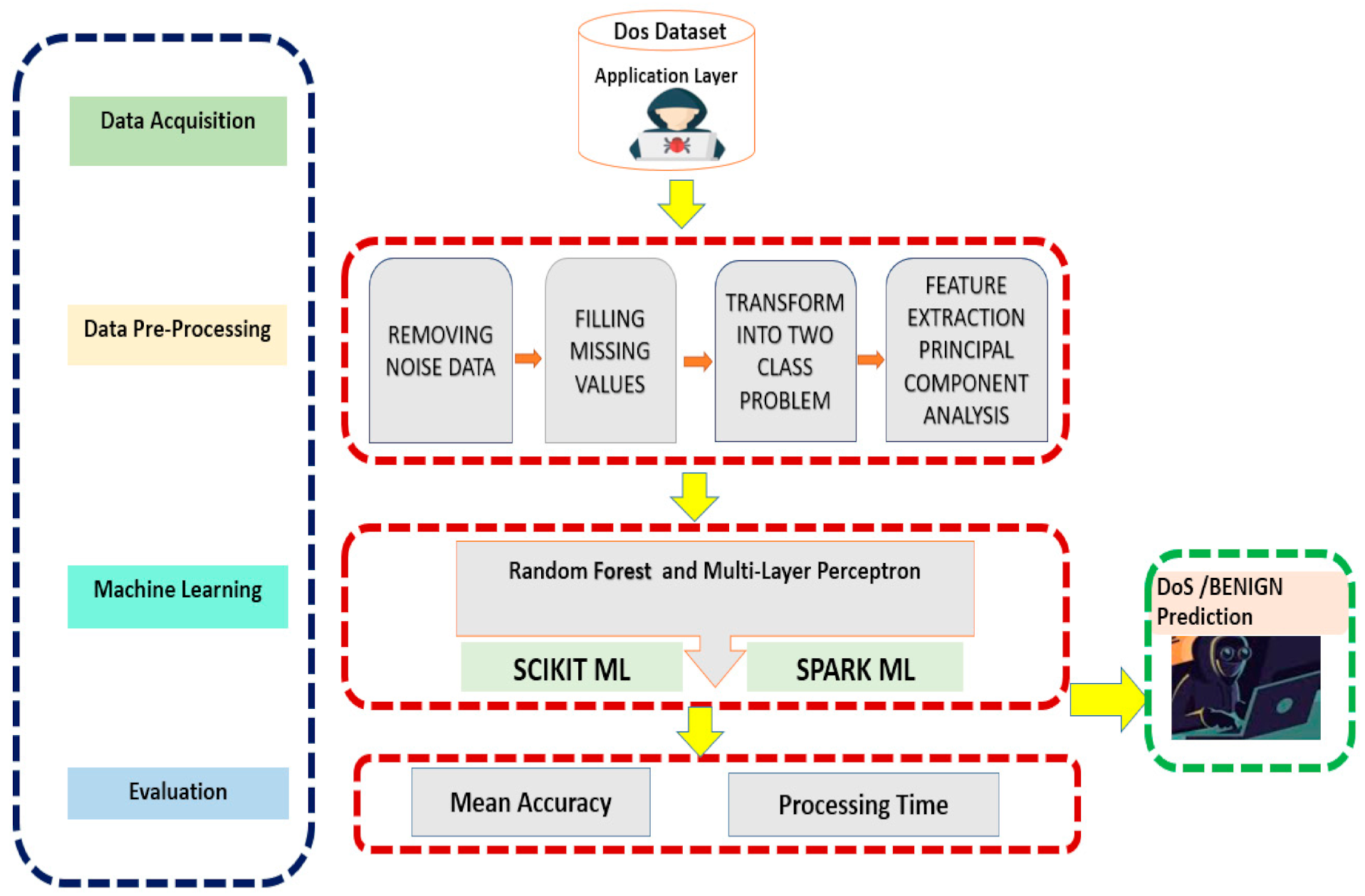
If this server error is. Even before you go and pull the server logs (more on that later) during a ddos attack, you’ll likely experience one or more of the following. To detect attacks, both types need to be independently monitored;
Certain ip addresses send too many connection requests over a short time. Dns request and dns response. Fill in the columns to send notification emails.
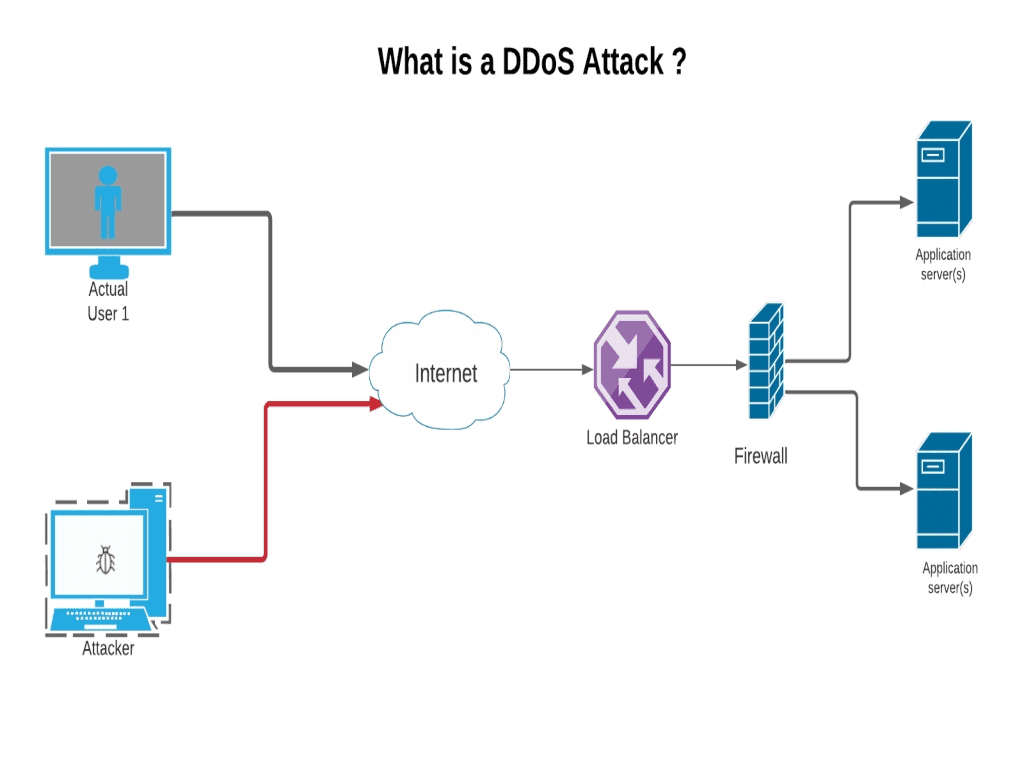
You see a surge in web traffic, seemingly out of nowhere, that’s coming from the same. Distributed denial of service (ddos) attacks is a subclass of denial of service (dos) attacks. How to know if you are under ddos attack?